Configuring the NSX Advanced Firewall service – Exploring Integrated Services Configuration
In this chapter, you will gain a comprehensive understanding of the intricacies involved in configuring integrated services. These services encompass the NSX Advanced security service, which offers a Layer 7 firewall and Intrusion Prevention System/Intrusion Detection System (IPS/IDS) security features. Additionally, you will explore VMware HCX, VMware Aria Operations for Logs, and the Tanzu Kubernetes Grid Service. By delving into these topics, you will acquire the essential knowledge required for your day-to-day tasks.
Specifically, this chapter covers the following topics:
• Configuring the NSX Advanced Firewall service
• The VMware HCX service
• VMware Aria Operations for Logs
• The Tanzu Kubernetes Grid managed service
Configuring the NSX Advanced Firewall service
The NSX Advanced Firewall service enables the following capabilities:
• A distributed IDS/IPS
• A distributed Firewall with the Layer 7 Application ID
• A distributed Firewall (DFW) with an Active Directory-based user ID – Identity Firewall (IDFW)
• A distributed Firewall with FQDN filtering
The NSX Advanced Firewall service further enhances the capabilities of the integrated distributed firewall, by providing end-to-end visibility and protection for the application traffic. This service protects both east-west and north-south traffic flows and offers additional protection against malware. From an architectural perspective, incorporating the NSX Advanced Firewall service into an SDDC is advisable when your design necessitates stringent compliance and security requirements, mandating end-to-end protection for application traffic. The NSX Advanced Firewall service is a paid service, billed per all the hosts in the SDDC when activated. The service cannot be activated on individual clusters in the SDDC. Organizations can choose between an on-demand rate, or one- or three-year subscriptions.
INFORMATION
Pricing information can be found at https://www.vmware.com/products/nsx-advanced-firewall-for-vmc.html.
To configure the NSX Advanced Firewall service, you need to perform the following steps:
- To activate the NSX Advanced Firewall service, navigate in the SDDC console to the Integrated Services section, and under NSX Advanced Firewall, click on ACTIVATE, as shown in the following screenshot:
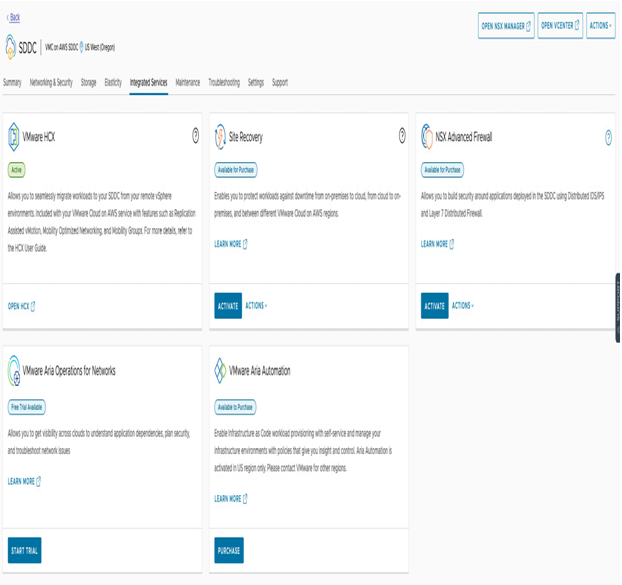
Figure 7.1 – Activating the NSX Advanced Firewall add-on
- Confirm the activation by clicking the ACTIVATE button on the following screen, as shown in the following screenshot:
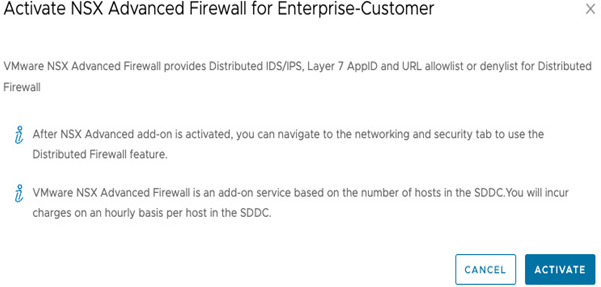
Figure 7.2 – Confirming activation
- Navigate to the Distributed IDS/IPS section under the Networking & Security tab to manage the newly activated Advanced Firewall service. On the initial deployment, confirm the steps required for activation by clicking on the GET STARTED button, as shown in the following screenshot:

Figure 7.3 – Distributed IDS/IPS
- Next, open the Settings tab, and enable the feature on the SDDC clusters by selecting them and clicking on ENABLE, as shown in the following screenshot:
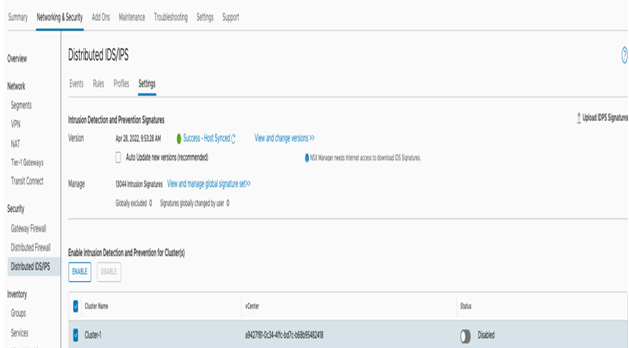
Figure 7.4 – Enabling distributed IDS/IPS on a cluster level
- Next, to enable the IDS/IPS inspection and prevention, organizations need to create policies and rules under the Rules tab. The rules must include an SDDC source or destination, and the rule cannot be just a broad all-encompassing any-any rule. The rule can work in Detect only mode to only prevent alerts or in Detect & Prevent mode to block attacks, as shown in the following screenshot:
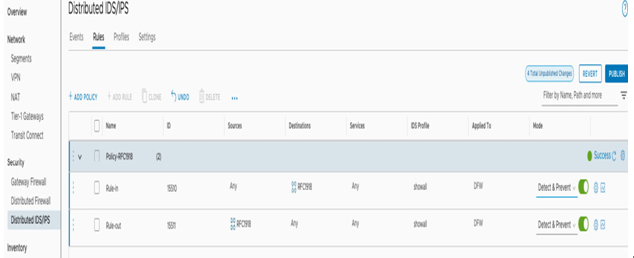
Figure 7.5 – Creating an IDS/IPS policy and rule
- Once the policy has been published, users can monitor the IDS/IPS activity and alerts under the Events tab, as shown in the following screenshot:
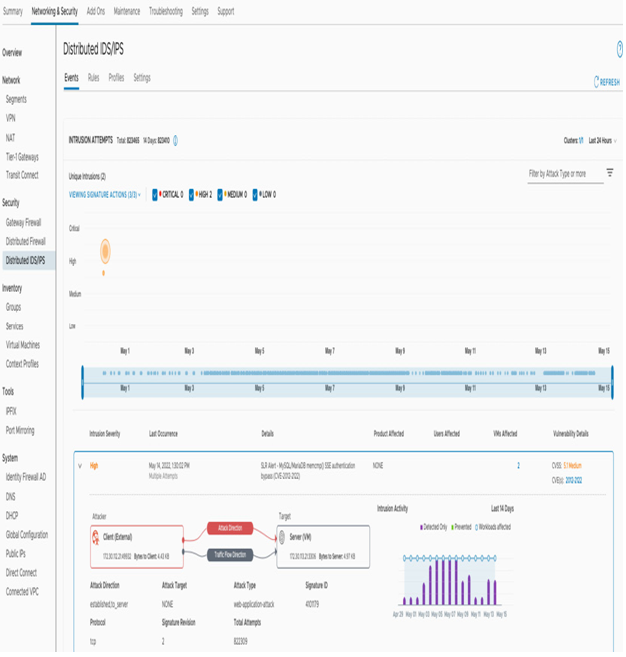
Figure 7.6 – Viewing the Distributed IDS/IPS Security Events
- FQDN and application-level rule filtering functionality is available upon activation of the service. Those rules are enforced in the Distributed Firewall section. To create an FQDN rule, users need to create an allow DNS snooping rule with DNS as a service and then add a block rule. The specific FQDN and app IDs are configured under the Context Profiles section – for example, with the Azure-Microsoft context profile, as shown in the following screenshot:
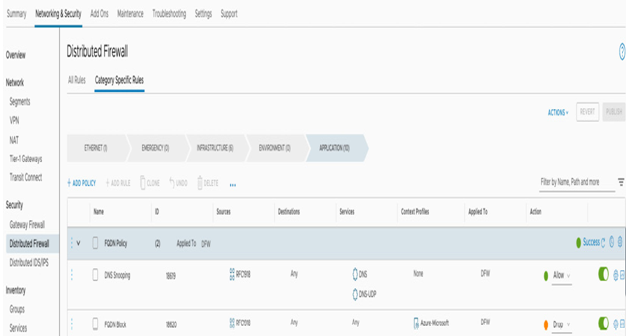
Figure 7.7 – A DNS FQDN filtering rule
- The FQDN and App IDs are configured under Context Profiles, under the Networking & Security tab, as shown in the following screenshot:
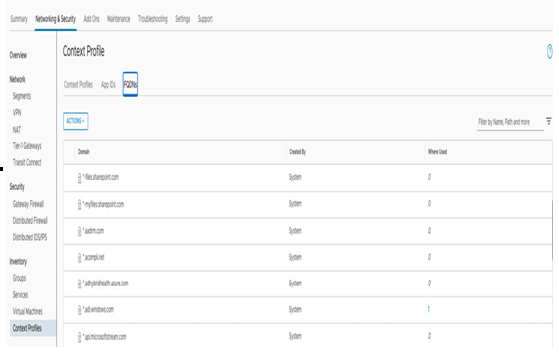
Figure 7.8 – FQDN configurations
- To incorporate attributes into a Distributed Firewall (DFW), users need to establish a new Context Profile and choose the FQDN and App ID attributes. To accomplish this, navigate to the Context Profiles tab, click ADD CONTEXT PROFILE, and select Set Attributes. Once the attribute is added, users should be able to see entries as shown in Figure 7.9:
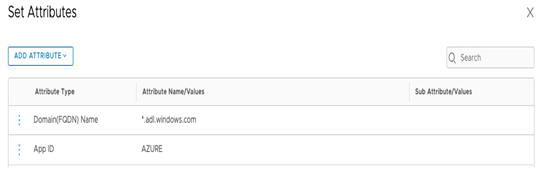
Figure 7.9 – Context Profiles – ADD ATTRIBUTE
- An Active Directory (AD)-based identity firewall is an additional capability of the service, which means that users can create DFW rules based on user identities, such as AD groups, as the source and destination, instead of IP addresses or VM names and tags. Users need to set up an Active Directory/LDAP identity source under Active Directory, under the Identity Firewall AD tab, as shown in Figure 7.10:
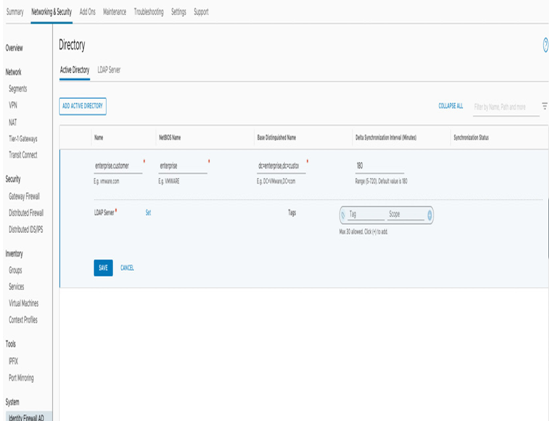
Figure 7.10 – Identity Firewall AD
- After configuring the identity source rules under the Distributed Firewall section, you can use AD Groups as the source/destination criteria in addition to the standard criteria, as shown in Figure 7.11:
Figure 7.11 – Adding AD Group as a member of the Compute Groups
NSX Advanced Firewall is a powerful service, enhancing security and compliance for your application workload deployed on a VMware Cloud on AWS SDDC.

